Penetration testing, often known as pentesting, is a multilevel security assessment conducted by a professional ethical hacker (Pentester) that uses a combination of machine and human-led techniques to identify and exploit vulnerabilities in infrastructure, systems and applications. A pentest can include black box, grey box or white box tests. After the pentesting, a post-assessment report is prepared by the pentester, in which he describes all the vulnerabilities as well as remediation guidance to resolve them.
Types of Pentesting :
- Internal/External Infrastructure and Network
- Web Application & Platform
- Mobile Application
- API
- Cloud
- Wireless
- etc.
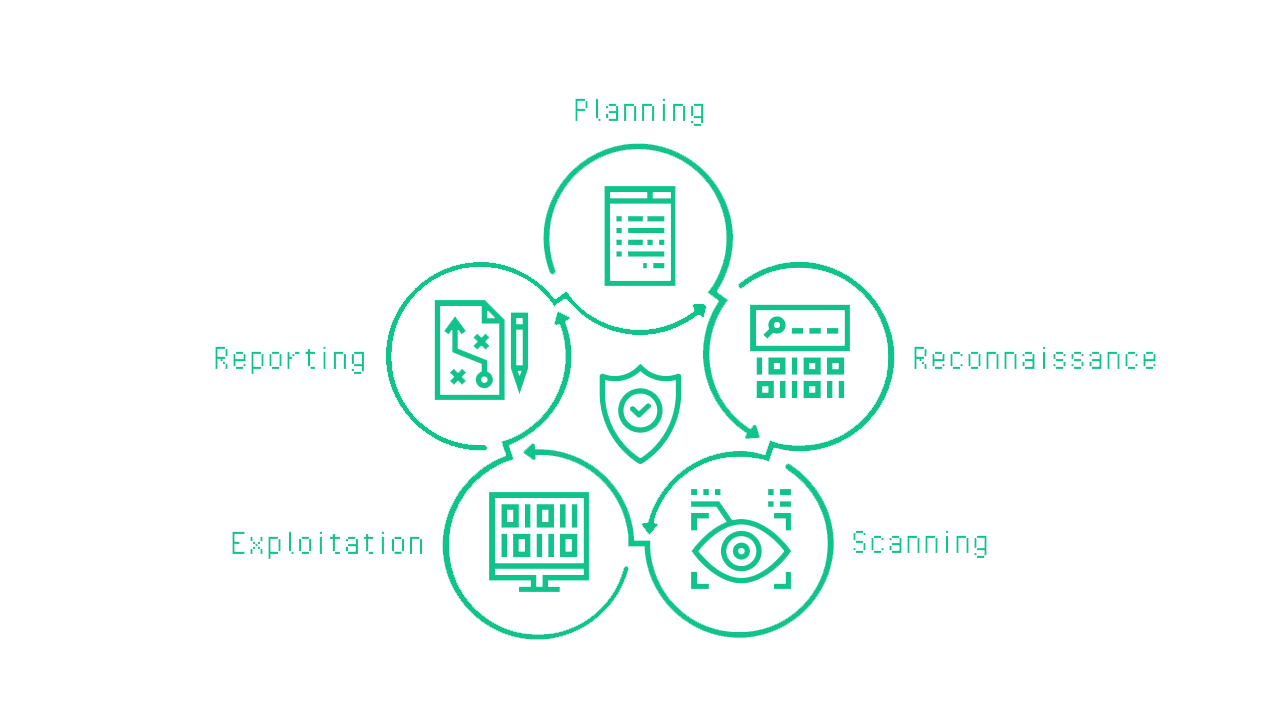
Penetration Test Methodology
A penetration test is based on a five-phase methodology : Planning, Reconnaissance, Scanning, Exploitation / Post Exploitation and Reporting. So let's have a look at these phases in detail.
Planning
This is the beginning of any penetration test. the steps of planning a pen-test are as follows : purpose of the pentest, identify the needs of the customer, target scope, type of test (white, gray or black box), pentest requirements (laptop, hdd/ssd, usb-stick, hacking hardware, tools/software etc.), backups, emergency response plan, contract agreement (rule of engagement and non-disclosure agreement), restrictions (out-of-scope, attack time, duration and methods ) and customer's budget.
Reconnaissance
In the phase of reconnaissance, we do active and passive information gathering on the target to gather data (open-source intelligence, network range, active machines, operating systems, open ports and access points, services on ports, map the network etc.) that we can use in order to better plan for attack. success of the test depends on the accuracy of reconnaissance. A pentester works on gathering as much intelligence on the client organization and the potential targets for exploits as possible.
Scanning
In the phase of scanning, we gather further intelligence of vulnerability and issues that are exploitable on the target. A vulnerability scan detects and classify system weaknesses and predicts the effectiveness of countermeasures.
Exploitation / Post Exploitation
Exploitation that's the phase that's also known as gaining access. It requires taking control of one or more network devices in order to extract data from the target, or use that device to launch attacks on the other targets.
The purpose of the post exploitation phase is to determine the value of the machine compromised and maintain control of the machine for later use. The value of the machine is determined by the sensitivity of the data stored on it and the machine's usefulness in further compromising the network.
Reporting
The report is the outcome of the actions performed throughout the pentest. the pentest report typically consists of the following sections : summary of purpose, scope, the duration of the pentest, detailed explanation of all the vulnerabilities we found during the pentest with screenshots to show how vulnerable it is and how the vulnerability is determined, vulnerability level (critical, high, medium or low), vulnerable assets, and recommendations to remediate and mitigate the vulnerabilities.
In the end it's very important to remove all these changes (new users, backdoor, file permissions, exploit/scripts etc.) at the end of the pentest so return everything to the initial state before the pentest.
Download pentest report sample from here.
